Lei Feng.com: This article was translated by Toopu Technology Engineer from How To Fool AI Into Seeing Something That Isn't There . Lei Feng network exclusive article.

Software engineers are also humans, and humans always make mistakes, so our machines are always full of security holes . When building the software that drives these computing systems, they may have code running in the wrong place, storing the data in the wrong place, or maybe they have stored too much data. The total number of security vulnerabilities has become a target for hackers, and they are not vulnerable when attacking.
But even if artificial intelligence replaces those software engineers, the risk remains. AI can also make mistakes, as described in a new paper published by Google and a researcher at OpenAI, a startup started by Tesla's founder Elon Musk. These risks are in new AIs that are constantly transforming our computer systems. It is very serious, especially when AI comes into contact with surveillance cameras, sensors and other electronic devices distributed around the world, they can become very high risk. "This is a question that everyone should think about," said OpenAI researcher, former Google employee Ian Goodfellow, who wrote the paper with current Google researchers Alexey Kurakin and Samy Bengio.
| See something that does not existWith the rise of artificial intelligence branch-deep neural networks that can learn scattered data by learning large amounts of data, we are moving toward a new trend: we will write more for the training machine than we directly let our computer perform services. The code.
In the leading Internet companies such as Facebook, Google and Microsoft, this trend has already become a reality.
Mark Zuckerberg and his company trained millions of pictures on the world’s most popular social networks to train human faces. Google uses a large number of spoken words to train neural networks to identify language instructions for Android phones. In the future, we will create intelligent robots and driverless cars.
Today, neural networks not only recognize objects, animals, signs, and other written languages, but they are also very good at recognizing faces and voices. But they also make mistakes—sometimes even commit some unimaginable mistakes. Kurakin said: "There is no perfect machine learning system." In fact, in some cases, you can trick these systems into thinking that they see or hear something that doesn't actually exist .
Kurakin explained that as long as the image is changed very finely, the neural network will think that this image contains something that it doesn't actually have. These changes may not be visible to the naked human eye . Sometimes the change is only in the picture. Several pixels are randomly added everywhere. He said that you can change a few pixels of the elephant's photo and then trick the neural network into thinking it is a car . Researchers like Kurakin call these "countermeasures." They are also one of the security holes in the neural network.
Kurakin, Bengio, and Goodfellow show in their new paper that even though neural networks are used to identify data directly from cameras or other sensors, the same loopholes may exist. Imagine if you have a system that uses a neural network-based face recognition technology to control the access privileges of a top-secret facility, Kurakin said, you can easily deceive it by simply drawing a few points on your face and let it Think you are the other person .
Goodfellow said that this type of attack can be used for almost any type of machine learning algorithms, not only neural networks, but also decision trees and support vector machines - those that have been popular for more than a decade to help machines learn from data Regular algorithm . In fact, he believes that similar attacks have already been practiced in the real world. He suspects that financial companies are likely to use these loopholes to deceive the trading systems used by their competitors. "They can fake some deals and trick their competitors to sell the stock at a price lower than the real value," he said. "Then they can buy stocks at low prices."
In their paper, Kurakin and Goodfellow deceive the neural network by printing a hostile image on a piece of paper and showing the paper to the camera. But they think that even smaller attacks can have effects—such as the previous example of adding a few pixels to the human face. Goodfellow said: “We are not sure what we can do in the real world, but our research shows that this is possible.†“We proved that we can deceive the camera, and we think there are a variety of attacks, including A face recognition system is deceived by adding human invisible markers, he added.
| Difficult to achieve a scamAlthough this is by no means an easy task, to deceive a neural network, you don't necessarily need to know how it is designed or what data it is trained on. As the previous study shows, if you can establish an adversarial sample to deceive your own neural network, it may also deceive other neural networks that handle the same task.
In other words, if you can fool an image recognition system, you may be able to fool another one. Kurakin said " You can use another system to make an antagonistic sample, and this sample will be more likely to deceive your neural network. "
Kurakin particularly emphasized that these are small security holes. He said that in theory they are a problem, but in the real world, precise attack is very difficult - unless the attacker draws the point on her face in the perfect mode, nothing will happen. However, this loophole is real. As neural networks play an increasingly larger role in the modern world, we must fill these loopholes. But what do you do - build a better neural network .
Although this is not easy, this work is in progress. Deep neural networks are designed to mimic the network of brain neurons, which is why they are called neural networks. But in the final analysis, they are just a large and complex mathematical operation - a layered calculus formula. This formula is formed by researchers like Kurakin and Goodfellow, and they are all human. In essence, they control these systems and they are already racking their brains to eliminate these security holes.
Kurakin said that one option is to add countermeasures to the neural network training set and teach neural networks to distinguish between real and hostile images. Researchers are also looking for other options, but they are not sure whether these methods have any effect. After all, to make neural networks better, we humans must first of all continue to make progress.
Lei Feng Network (Search "Lei Feng Network" public number concerned) Note: Reprinted please contact us to authorize, and retain the source and author, may not delete the content.
ST Series Single Phase Alternator
ST Single Phase Alternator Suppliers
The construction of the generators is of drip-proof, salient pole rotating field self excitation and constant voltage type. The alternator interior is used with high quality electric magnetic and Electric materials. Stator insulation is class B. These generators are elegant in appearance, tight in construction and easy maintenance. IEC standard are adopted on dimension, these dimension are suitable for using in Australia, Europe, America and other countries with the end covers to be model B.
The alternators are of harmonic wave self-exciation constant voltage system and automatic voltage control excitation constant voltage system, both of them have Excellent dynamic performance, convenient and reliable in operation. These generators are excellent in appearance and easy to maintain. Dimensions are adopted according to I.E.C Standards.
The voltage of the alternator is 230V of 115V, the frequency is 50Hz. Its operation mode is of continuous duty. It can provide 60Hz and the other voltage's generator according to necessary.
The alternator can be coupled with a prime mover directly or through a V-belt, with 5% change of speed of the prime mover under load Variation of 0~100%, at a voltage of 230V or 115V, 50Hz or 60Hz to get a satisfactory constant voltage performance.
Operating Condiyions:
1. Altitude: not exceed 1000m.
2. Cooling air temperature: 258~313K 3. Relative air humidity: not exceed 90%.

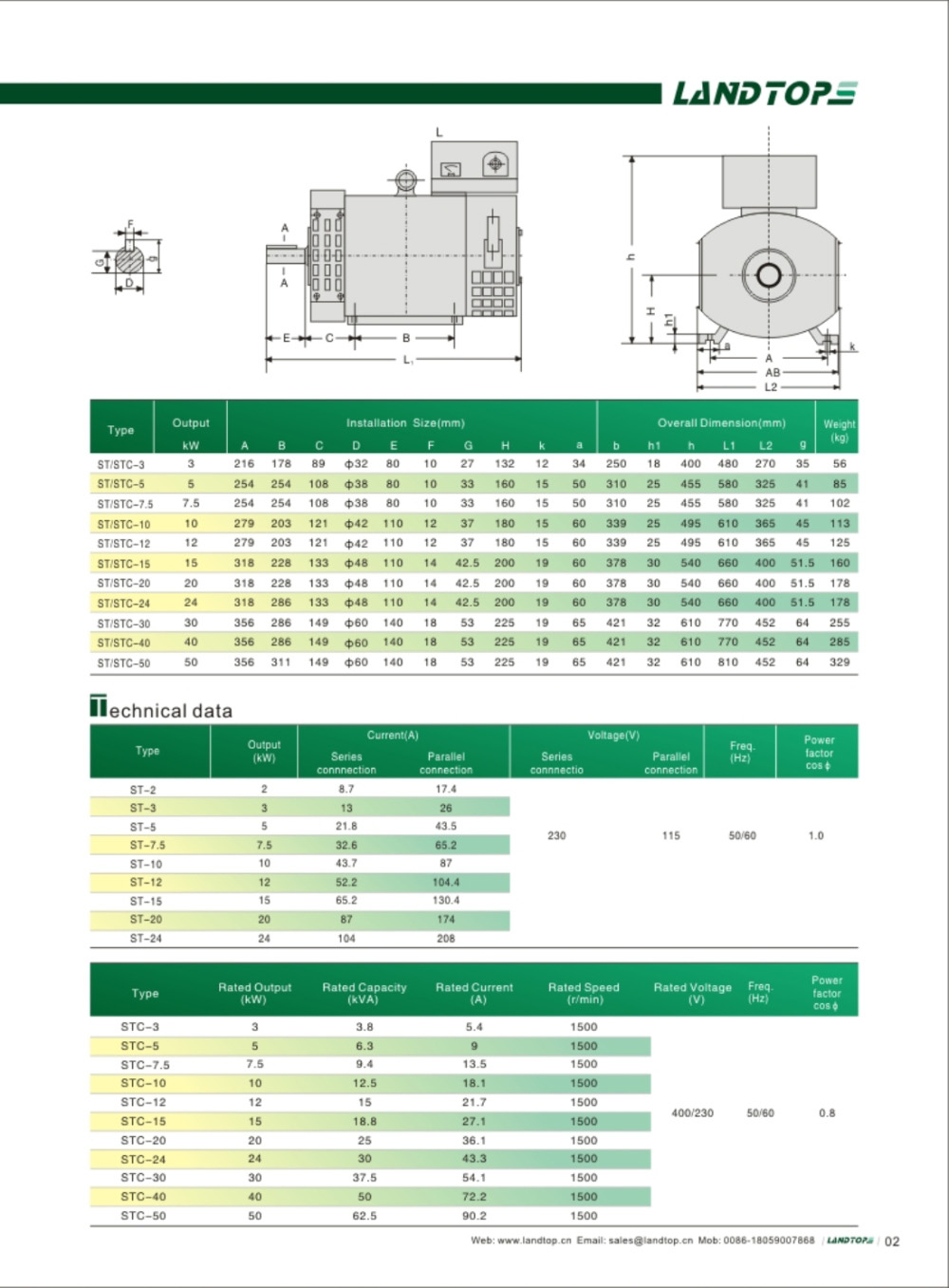
ST Series Single Phase Alternator,Single Phase AC Generator,Single Phase Ac Dynamo,240 Volt Alternator
FUZHOU LANDTOP CO., LTD , https://www.landtopco.com