Despite the growing importance of smart home security, regulations and standards are still not fully developed. Many people remain unaware of the potential risks associated with smart devices, and companies often prioritize cost control over robust security measures. This has led to weak security in many smart home products, yet safety continues to be a major concern among consumers and industry experts alike. Security requirements include access control for authorized users, user authentication, data integrity, privacy protection, secure data transmission, and proper authorization management. At the core of the IoT supply chain, the upstream components—such as security IoT modules and secure platform access capabilities—play a critical role in determining the overall security of downstream hardware. Whether using software or hardware encryption, what matters most to users is whether their devices are truly secure. For businesses, security is essentially a quality issue, and it should be integrated into the product development lifecycle to ensure that IoT products meet high-security standards.
Ai Wei Technology's GIANT-I is the world’s first PUF-based encryption chip, designed to provide a highly secure solution for IoT devices. By integrating VIA PUF technology, this chip uses the unique physical characteristics of its microstructure as an encryption key, making it nearly impossible to clone. The combination of hardware SHA-2 algorithms and PUF key encryption ensures that software systems are protected from copying, consumables are authenticated to prevent counterfeiting, and network nodes are verified to maintain data integrity and prevent tampering. Unlike traditional encryption keys, the PUF key is generated on demand and does not need to be stored, offering a more secure and efficient approach to data protection.
Congru Technology’s Tianchang SIC Smart Intrusion Immune Chip (SIC) is a powerful security solution that enhances the protection of smart devices and cloud services. It supports two-way identity authentication, symmetric key exchange, and secure communication between smart devices and the cloud. Integrated with intrusion prevention and threat awareness technologies, the SIC works in conjunction with backend IoT threat intelligence to create a strong defense against cyber threats. The SIC comes in two models: SIC120, which is ideal for Wi-Fi-enabled smart devices, and SIC500, suitable for devices with 2G/3G/4G connectivity. These chips are designed to be either parallel or serially connected, depending on the device configuration, ensuring maximum security at every level of the network.
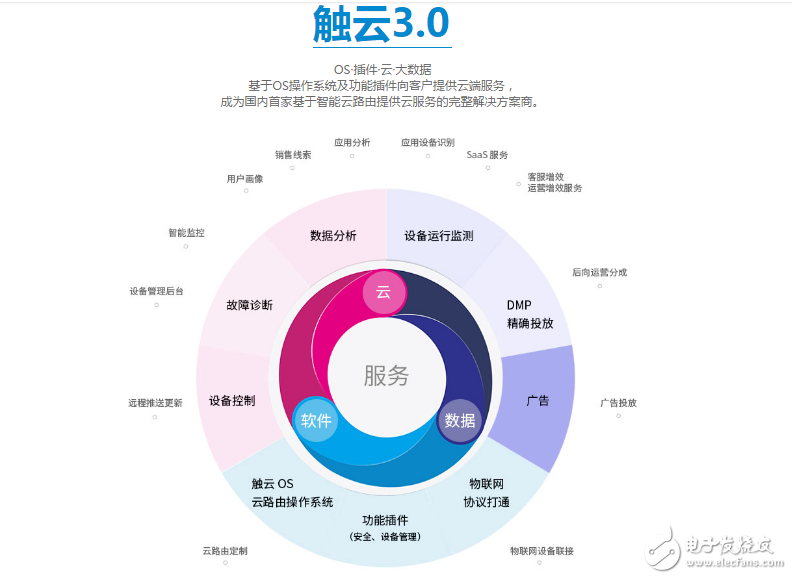
Touch Cloud Technology’s Intelligent Routing OS 3.0 is a groundbreaking solution that redefines the role of smart home gateways. As the central hub of the smart home ecosystem, it prevents ransomware and other malicious attacks from compromising the system. Designed as the first open intelligent routing operating system, it includes a comprehensive set of functional modules, hardware reference designs, and cloud-based customization options. Since its launch in 2014, Touch Cloud OS has evolved through multiple updates, reaching version 3.0. This latest iteration integrates advanced cloud services, with 80% of operations handled in the cloud and 20% on the router itself. This approach reduces hardware costs while enabling endless possibilities for value-added applications. Additionally, the SDPI technology used in the cloud ensures high performance without increasing hardware expenses.

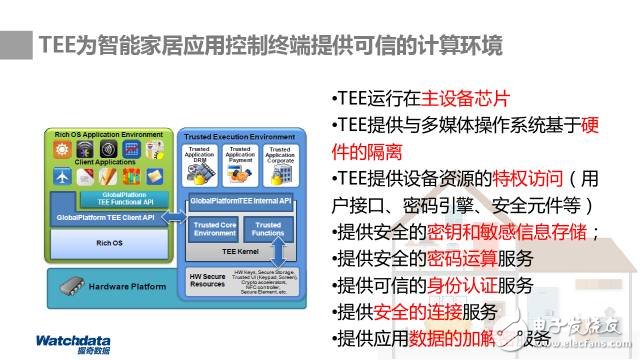
Smart home security solutions built on SE (Security Module), TEE (Trusted Execution Environment), TAE (Trusted Application Environment), TSM (Trusted Service Management), TAM (Trusted Application Management), and KMS (Key Management System) technologies offer a comprehensive approach to securing IoT ecosystems. These solutions are particularly effective for smart home gateways, cameras, door locks, and other connected devices. By leveraging these advanced security frameworks, companies can ensure secure authentication, data protection, and trusted execution environments, significantly reducing the risk of cyberattacks and unauthorized access. The integration of these technologies allows for seamless, secure interactions between devices and cloud platforms, enhancing both usability and safety in the smart home environment.
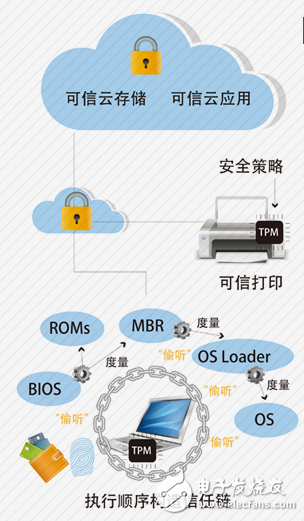
National Technology is a leader in information security, specializing in security chips, identity authentication, and network credibility. With a long history of innovation, the company provides a wide range of information security services to both government agencies and commercial organizations. These services include mobile identity authentication, e-banking, data encryption, e-government, and financial transactions. National Technology is known for its network identity security chips, trusted computing solutions, and personal digital security products. One of its most notable contributions is the RCC controllable distance safe communication technology, which has over 800 global patents and is recognized as an industry standard by the Ministry of Industry and Information Technology. The RCC national standard has been widely adopted, with over 9 million users worldwide. Its innovative Bluetooth SIM products have also found applications in secure areas such as mobile banking and blockchain, further expanding the reach of its security solutions.
electric bike charger,ebike charger,Sweeper charger,charger for vacuum cleaner
FOSHAN SHUNDE KELICHENG POWER SUPPLY TECHNOLOGY CO., LTD , https://www.kelicpower.com