Despite the growing importance of smart home security, regulations and standards are still not fully developed. Many people remain unaware of the potential risks, and companies often prioritize cost control over security. This has led to a weak security awareness among enterprises, especially in the smart home industry. However, safety is becoming an increasingly hot topic due to the rising number of cyber threats and data breaches. Security requirements include ensuring access by authorized users, verifying user authenticity, maintaining data integrity, protecting privacy, securing data transmission, and enforcing proper authorization controls.
Currently, the upstream segment of the industry chain focuses on secure IoT modules and platform access capabilities, which play a critical role in determining the overall security of downstream products. Whether using soft or hard encryption methods, the ultimate concern for users is whether the system is safe. For businesses, security is not just a feature—it's a quality issue. Therefore, during the product development phase, security should be a core part of the evaluation process, ensuring that IoT devices meet high-level protection standards.
Ai Wei Technology’s GIANT-I is the world’s first PUF-based encryption chip, designed to offer superior security. It integrates VIA PUF technology, making it a high-security, high-performance encryption solution. Unlike traditional encryption methods, GIANT-I uses the unique physical structure of the chip as an encryption key, which is generated on demand and never stored. This ensures that the key is unclonable and highly secure. The chip combines hardware SHA-2 algorithms with PUF key encryption to protect software systems from copying, authenticate consumables and accessories, and ensure the integrity of network nodes. Its robust design provides a more reliable and secure approach to data protection.
Congru Technology’s Tianchang SIC Smart Intrusion Immune Chip is a breakthrough in secure communication for smart devices. The SIC (Smart Intrusion Immunization Chip) works with the Smart Device Secure Bearer Protocol (Schain) to enable two-way identity authentication, secure key exchange, and encrypted data transmission between smart devices and cloud platforms. By integrating intrusion prevention and threat awareness technologies, the SIC enhances the security of IoT ecosystems. It offers two models—SIC120 for Wi-Fi-enabled devices and SIC500 for 2G/3G/4G-connected devices—each tailored for different integration needs. This makes it a flexible and powerful solution for securing smart environments.
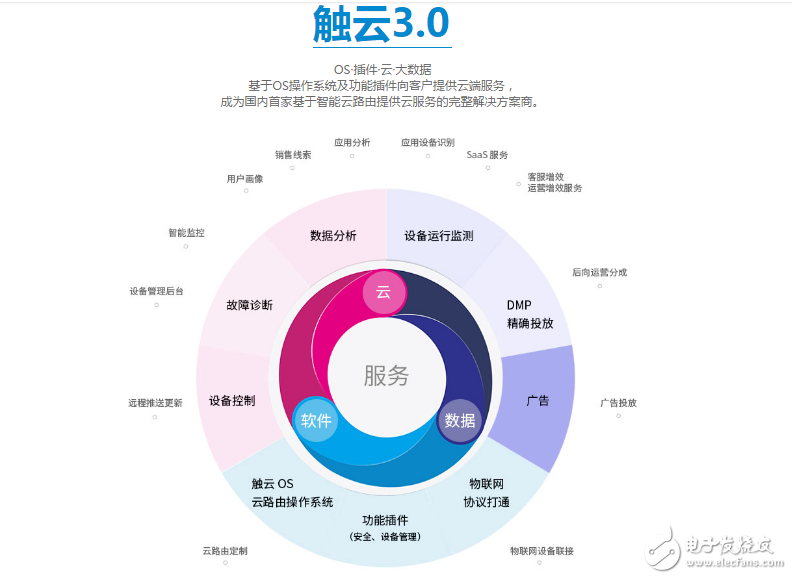
Touch Cloud Technology’s Intelligent Routing OS 3.0 is a groundbreaking solution for smart home gateways. As the central hub of a smart home system, it prevents ransomware and other malicious attacks from compromising the network. Touch Cloud OS 3.0 is the first open intelligent routing operating system that integrates cloud services, allowing 80% of operations to take place in the cloud while 20% run locally. This reduces hardware costs and opens up endless possibilities for value-added applications. With its SDPI technology, it delivers high-performance services at a lower cost, making it ideal for modern smart homes.

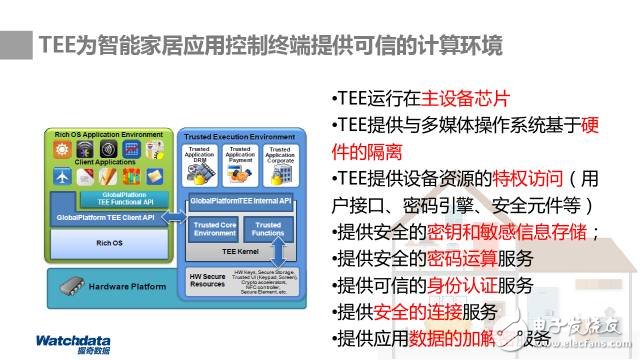
Smart home security solutions based on SE (Security Element) and TEE (Trusted Execution Environment) technologies are gaining traction as the need for secure IoT ecosystems grows. These solutions provide comprehensive protection for smart devices such as gateways, cameras, and door locks. Companies leverage their expertise in SE, TEE, TAE, TSM, TAM, and KMS to deliver end-to-end security across various smart home applications. By integrating these technologies, they ensure secure data handling, user authentication, and trusted execution environments, offering a solid foundation for future smart living.
National Technology is a leading provider of information security services, specializing in security chips, identity authentication, and network credibility. Their solutions support a wide range of applications, including mobile identity authentication, e-banking, data encryption, e-government, and financial transactions. National Technology is renowned for its RCC controllable distance safety communication technology, which has over 800 global patents and is recognized as an industry standard. The RCC national standard has been widely adopted, with over 9 million users. Their innovative Bluetooth SIM products are also being used in emerging fields like mobile banking and blockchain, demonstrating their commitment to advancing digital security.
Hydrogen-rich Water Machine Power Supply
Electrolytic Water Machine Power Supply,Electrolyzer Power supply,Hydrogen Water Generator Power Supply
FOSHAN SHUNDE KELICHENG POWER SUPPLY TECHNOLOGY CO., LTD , https://www.kelicpower.com