Previous Understanding
Before I started working in the IT industry, I believed that securing a server was as simple as changing the password to something complex, altering the SSH port from the default 22, and ensuring that only authorized personnel could log in. I thought that was enough to keep everything safe.
Current Understanding
After working for several years, I faced a real security incident where our server was hacked, the website suffered a DDoS attack, and the database was tampered with. That experience changed my perspective completely. I realized that just keeping people out isn't enough—IT security is a much broader and more complex topic than I had previously understood. The more I learn, the more I realize how little I actually know.
Let me share my thoughts on IT security.
1. Network Security
Many companies don’t implement third-party audit systems or analyze logs effectively. In fact, an audit system can trace operations and provide valuable insights, which is far more useful than verbal reports. My company recently purchased a log audit system, but it wasn’t very effective. As a result, I set up an ELK stack to monitor server logs and detect suspicious activities. This approach has worked well, and even developers use similar systems to track application behavior and ensure compliance.
Here’s a screenshot of my ELK setup for monitoring server operations:
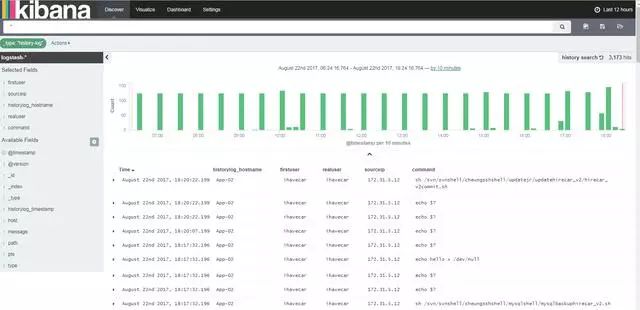
Network security covers many areas. For example, using ARP binding can prevent ARP spoofing attacks. You can also invest in intrusion detection and prevention systems, firewalls, and regularly update network device passwords. Configuring authentication failure handling, session timeouts, and using HTTPS for encrypted communication are all essential practices.
In addition, regular self-assessments such as vulnerability scans, weak password checks, and baseline configuration reviews should be conducted. These help identify open ports, weak passwords, and known vulnerabilities in both the host and applications. Scanning for malware and analyzing results can improve overall security management.
2. Host Security
Many organizations lack host-based intrusion detection systems (HIDS), which can detect unauthorized access to critical servers. These systems can log attacker details like IP address, attack type, and time. While hardware solutions like WAFs or IPSs are common, they may not be affordable for smaller companies. However, free tools like OSSEC or HIDS can still provide real-time threat detection and malware removal.

Host security also includes secure system configurations, strong authentication mechanisms, and password policies. For instance, limiting failed login attempts can prevent brute-force attacks. Password complexity requirements should avoid predictable patterns like keyboard sequences. Critical servers should enforce mandatory access controls at the kernel level, restrict default account access, and change default passwords whenever possible.
3. Application Security
a) Implement multi-factor authentication for user identity verification.
b) Enforce password complexity rules, such as requiring a mix of letters and numbers, and limit password length to 8–20 characters. Change passwords every six months.
c) Limit login attempts to 5 per hour and lock accounts after multiple failures.
d) Ensure users meet password complexity requirements and have login failure handling enabled.
e) Apply sensitive tags to important data resources. If the system doesn’t support this, use dedicated security devices to enforce access control.
f) Enable comprehensive security audits that track all user activities and their actions.
g) Ensure audit logs cannot be altered or deleted by non-administrators.
h) Limit concurrent sessions for each user to prevent resource exhaustion.
i) Set limits on the number of requests or processes per account.
j) Allow priority access based on security policies and allocate resources accordingly.

4. Data Security and Backup Recovery
a) Implement off-site data backups and transfer critical data to a secondary location regularly.
b) Use hardware redundancy for key network equipment and data systems to ensure high availability.
c) When importing production data into test environments, apply data masking to protect sensitive information like credit card numbers and phone numbers.
d) Control data access through strict procedures. Non-ops personnel should only get read-only access, and their actions can be monitored via a bastion host or by disabling clipboard functions.
e) Regularly upgrade your database, even if it's internal. Malicious code or backdoors can compromise the system, and many databases have hundreds of vulnerabilities that aren’t fixed by patches alone. Upgrading to the latest stable version is the best solution.

5. Web Business Security
a) Set a reasonable session timeout to reduce the risk of session hijacking. Clear session data once the timeout occurs.
b) Limit the number of concurrent sessions per user to prevent resource exhaustion and malicious activity.
c) Use SSL/TLS for secure communication between clients and web servers. Ensure proper configuration with strong encryption algorithms and key lengths.
d) Log all critical events, including abnormal logins, malicious code deployment, and changes to user accounts or administrative actions.
e) Maintain a detailed code review process before and after upgrades, and document any issues found during audits.
f) Avoid transmitting passwords in plain text. Use SSL tunnels to encrypt sensitive data during transmission.
g) Implement two-factor authentication for critical operations like password changes, account recovery, or mobile number updates to prevent identity theft.
h) Avoid revealing specific error messages when authentication fails. Provide generic error responses to prevent attackers from exploiting them.
i) Enforce password policies at the system level, including minimum length, complexity, and expiration periods, especially for admin accounts.
j) Implement account lockout policies that temporarily block users after multiple failed login attempts, with configurable unlock times.
k) Protect sessions against tampering, replay attacks, or forgery using secure session management techniques.
connectors of car antenna,consisting of antenna,High Frequency Oscillator
Mianyang Ouxun Information Industry Co., Ltd , https://www.ouxunantenna.com